At Dispatch, a lot of what we do is in the Enterprise HR systems world. And in that world, Workday is currently the hottest HRIS. Thousands of companies across all industries are adopting Workday as the new core of their HR systems. For many enterprises, Workday is the first truly modern cloud-based HCM/HRIS platform. While Workday itself is a comprehensive solution, unlike legacy systems that live behind the firewall, Workday’s cloud-centric model enables the creation of a rich ecosystem of solutions that span across the entire people management spectrum.
The value of a rich app ecosystem cannot be underestimated. Companies now have the ability to tailor best-of-breed solutions to work together in harmony by building intelligent data integrations. This new approach to business IT infrastructure provides customized value for each company that individual monolithic solutions can’t. App ecosystems are devised to meet a company’s unique needs and can evolve quickly to adapt to changing business requirements. Each ecosystem is like a company’s IT fingerprint, and in the HCM world, this is becoming a core part of creating differentiated employee lifecycle experiences.
The evolution from monolithic solutions to cloud-based ecosystems is creating a transformative opportunity to increase efficiency and add value. However, the cloud-centric world does introduce new challenges for CIO’s and other business leaders. As cloud-based app ecosystems like Workday’s have become the norm, addressing issues like Complexity, Security and Reliability has become increasingly urgent.
Complexity
One of our Workday clients has over 190 integrations to third-party applications and services, and the integrations between Workday and these systems run over 40,000 times each month. While that’s an extreme case (they are one of the largest Workday instances globally), it does point to the emerging challenge of managing the complex job of keeping dozens (or hundreds) of applications flying in formation.
Quite often app ecosystems evolve into a complex and poorly understood mishmash of applications. Individual departments or functions can drive the acquisition of SaaS solutions to meet their specific needs, and organizations can lose control of the overall architecture. This may not seem that important as long as departments are getting what they need, but there are some things to be mindful of. Each individual system is typically a consumer of data from other applications, a transformer of data, and a transmitter of data to other systems. Therefore, it is important to understand:
What are the “systems of truth” for each type of data?

There should only be one for each type of data. Multiple systems of truth violate Segal’s law; “a person with one watch knows what time it is. A person with two watches is never sure.”
Without clearly defining which application is the source of truth, as well as who and how that truth is defined, data can easily be modified and stored in multiple applications. This undermines the ability of an organization to determine what data is correct. Users will quickly lose trust in systems that seem to have conflicting data. Incorrect data undermines the essential value of the app ecosystem and can lead to costly errors that get propagated throughout an organization, and can be extremely difficult to fix.
How do applications interact with each other, and what workflows span multiple systems?
Workflow mapping is important to understanding dependencies between applications. In a complex app ecosystem, when something goes wrong, integrations begin to fail, or data quality seems to be deteriorating, a clear architectural map is valuable for root-cause problem-solving. This map is also helpful when upgrading or changing systems, so upstream and downstream implications are fully understood. That map should include primary applications – but don’t forget about details such as SFTP site dependencies.
If an application is upgraded, replaced or reconfigured, how can we be sure we don’t break workflows across dependent systems?
If you have a few dozen SaaS apps or more in your app ecosystem, you can count on the fact that at any point in time, at least one of the applications across your solutions portfolio is being upgraded, reconfigured, or replaced completely. Workday itself has two new releases a year in March and September. Each time an application changes, there is a risk that a change might break an upstream or downstream process and disrupt an essential workflow. While SaaS companies generally do a good job of testing their applications, they can’t possibly validate every possible use-case unique to you.
The upgrade treadmill is one reason why having the above issues in control is so important. Understanding the sources of truth for each data type, how the data is used in each of your applications and what workflows are dependent on what application will make your life far easier during upgrade cycles and app replacement projects. You can be far more efficient in designing and executing the regression testing your business needs when apps change to be sure workflows will never be disrupted and data quality will be assured.
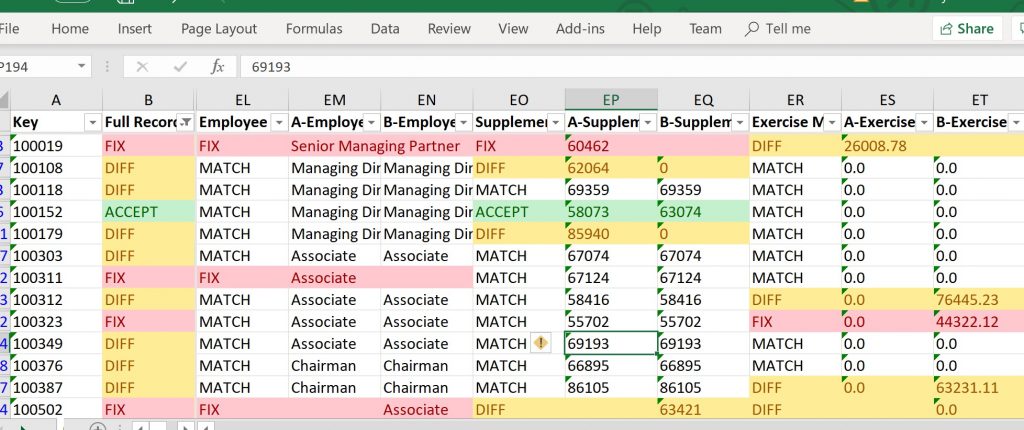
Dispatch has developed a new tool, Compare to help business analysts and integration specialists verify that data hasn’t changed as a result of an application change. Compare is a super-simple tool that does one thing really well: compare the data between two CSV files, and flag data that is different. Compare does this job really fast, even if there are millions of records in a file. The output is generated into an excel file, where further manipulation can be performed.
There are lots of different situations where an analyst may want to compare two CSV files. In particular, when applications are upgraded or replaced, it is critical to quickly determine if data migrated successfully and completely between applications (if an application is replaced), or if the new version of an application outputs exactly the same data as the old version did (when doing upgrade regression testing). Compare takes a tedious job that can take hours to complete, and instead does it in minutes.
Security
Data security is a massive concern for companies of all sizes. And integrations between cloud applications can expose vulnerabilities in an overall security framework. Two of the largest areas of concern regarding security in an enterprise’s integration portfolio are Identity Management and Data Security in Flight.
Enterprise Identity Management

It isn’t uncommon for employees to need access to 10 or more systems to do their jobs. Securely provisioning, managing and revoking access to these systems is a huge priority for all enterprises. Identity management is still an evolving science, and not all SaaS providers support an enterprise’s standard. Services from companies such as Okta have emerged to try to simplify identity management and give companies comfort that only authorized individuals have access to the data stored within their applications. The fact that Okta IPO’d for over $1.5B in 2017 and has a market cap ten times that value less than two years later shows how important this issue has become. Integrations with Okta and similar tools are now a fundamental part of most new Workday projects we see.
Data Security in Flight

A few years ago, executives were comforted with the concept that all their data resided behind impenetrable corporate firewalls (well, how impenetrable they were is up for debate). Today, you may trust Workday’s security protocols to keep data safe within their system. But that’s not enough. It’s unnerving to know that terabytes of a company’s most confidential and sensitive information flow freely every day via the open internet, whisked between a multitude of SaaS applications, none of which is in the company’s direct control. It can be more unnerving to realize there is probably no-one in your company who can definitively state that all this data is flowing in a secure and encrypted fashion.
Integrations can be a significant weak point in a company’s data security framework. We have seen integrations built without any encryption at all or encrypted with weak standards. We have seen unencrypted CSV files dropped on unsecured FTP servers for applications to pick up. We have seen integrations built with credentials embedded directly in the integration code for any developer to see. We have seen good encryption defeated when employees and service providers share credentials over unsecured channels such as email.
In short, data security for many cloud-to-cloud integrations is a mess. Most CIO’s cannot give their executive team confidence that all their most valuable data flowing between applications is properly encrypted, fully secured, and guaranteed to be delivered “as-sent” to downstream applications and third-party service providers.
Dispatch is building our own solution, Sentinel to help companies become confident in their data in flight. Sentinel is designed to check data while it’s in transit between applications, to validate encryption is in place. It also uses statistical analysis and learning to check to see if the data makes sense. Is the data format the same as the last time the file was sent? Are there a similar number of records? Are there expected frequencies of record changes for critical fields Sentinel checks the business-level parameters of files in flight, and alerts the business to potential issues before bad data lands in a downstream system where it can cause significant harm.
In addition to using a tool like Sentinel, management must insist on integration security audits. They must understand how data is encrypted in flight, what additional security methods are used to protect that data, and what protocols are in place to protect the credentials to the security methods.
Reliability

As the number of integrations grows, the importance of these integrations working right every time also grows. Businesses can grind to a halt if data can’t flow between applications. While each application may have good uptime statistics, overall reliability for cross-system workflow is a function of the number of applications involved (including middleware), and transient network conditions. A system of 20 applications, middlewares, SFTP sites and network nodes that each have 99% uptime result in only 80% system reliability.
Reliability is also impacted by data quality. Malformed or incomplete data can cause integrations to fail outright, or more frequently finish with errors or warnings. Outright failures can lead to delays in business processes completing…such as running payroll. Dealing with outright failures due to malformed data seems pretty straight forward – fix the data problem and re-run. However, most times, these types of failures require some form of forensic investigation to figure out exactly what happened, and that can take time. Integrations that complete with errors or warnings are more insidious. It’s easy to put fixing those errors on a backburner. However, ignoring errors and warnings can mask more serious problems. We advise that these issues be addressed as they occur.
The worst kind of failure is when the integration completes, appears to be successful, but in fact, the wrong data was actually transmitted. We’ve seen obsolete or test data transmitted in production environments and get ingested by downstream systems. This type of error can be very difficult to pick up until it’s too late, with sometimes disastrous consequences to the business – especially if the data is payroll or financial in nature.
We’ve developed a number of tools and methods to improve the ability for companies to be informed and alerted to integration reliability issues. Sentinel is a lightweight dashboard developed by Dispatch that monitors integration health in real-time. This tool gives users the ability to visualize historical integration performance to look for trends and patterns, as well as the ability to keep an eye on integrations that are currently in flight. Sentinel is designed specifically for Workday integrations and it can be connected directly to ticketing systems where it can generate prioritized alerts if integrations fail based on the type of failure and the importance of the integration.
The App ecosystem opportunity
Overall, we’re huge fans of this new cloud-centric enterprise application world. We believe it truly unlocks value for organizations that was impossible to contemplate before now. And we believe the new organic IT infrastructures being created can rapidly adapt to change as new solutions emerge and business requirements evolve. The shift towards the cloud is fundamentally good for business, but business leaders do need to be proactive in addressing new challenges in managing complexity, security and reliability. Thankfully tools and methods to manage these issues are improving every day.
To learn more about how Dispatch can help build and manage your cloud-based app ecosystems, please reach out to us here!
Cameron Hay is the CEO of Dispatch Integration, a data integration and workflow automation company with clients in Canada, US, Europe and Australia. He has over 30 years of leadership experience in various technology-oriented industries.